How To Enable 802.1 X On Windows 10
This document describes how to set up a Wireless Local Area Network (WLAN) with 802.1x security on an Cisco Goad 9800 Series Wireless Controllers by Graphic User Interface (GUI) or Command Line Interface (CLI).
Requirements
Cisco recommends that y'all have noesis of these topics:
- 802.1x
Components Used
The data in this document is based on these software and hardware versions:
- Catalyst 9800 Wireless Controller Series (Catalyst 9800-CL)
- Cisco IOS-XE Gibraltar 16.x
The information in this certificate was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, ensure that you understand the potential impact of any control.
Network Diagram
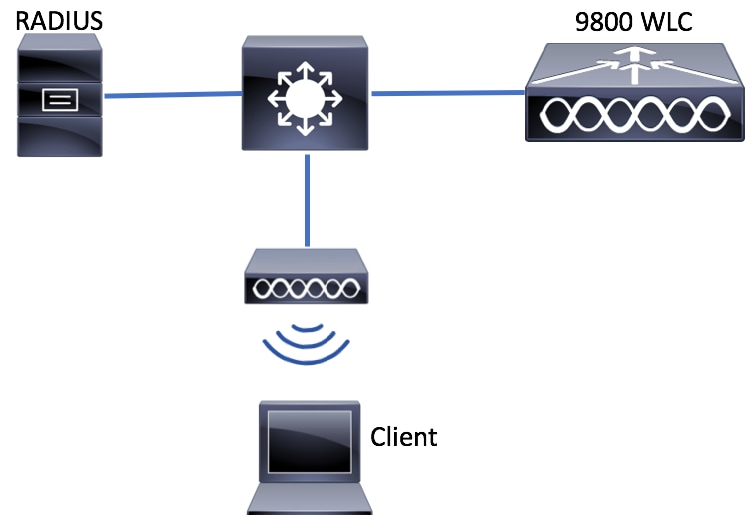
Configuration
AAA Configuration on 9800 WLCs
GUI:
Stride one. Declare RADIUS server. Navigate toConfiguration > Security > AAA > Servers / Groups > RADIUS > Servers > + Add togetherand enter the RADIUS server's data.
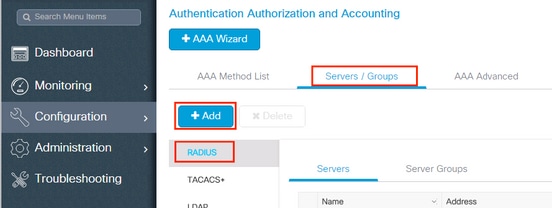
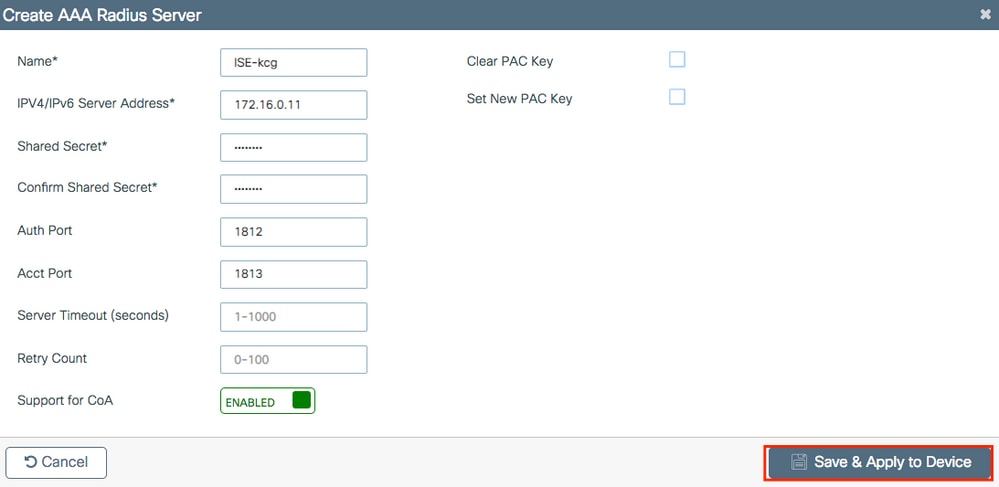
EnsureSupport for CoAis enabled if you plan to use Cardinal Spider web Authentication (or any kind of security that requires CoA) in the time to come.
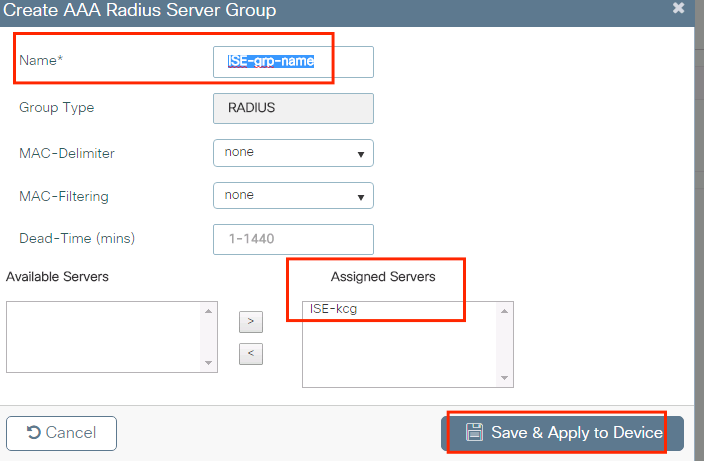
Step ii. Add together the RADIUS server to a RADIUS group. Navigate toConfiguration > Security > AAA > Servers / Groups > RADIUS > Server Groups > + Add together.
Step 3. Create an Authentication Method List. Navigate toConfiguration > Security > AAA > AAA Method List > Authentication > + Add together
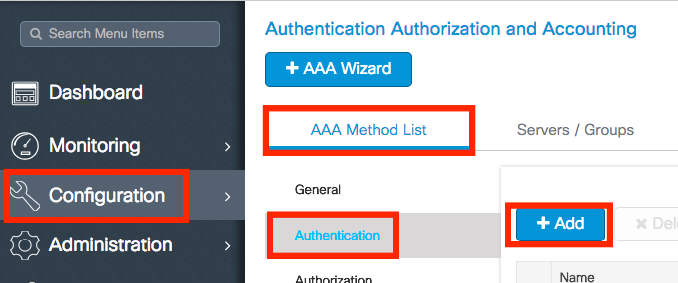
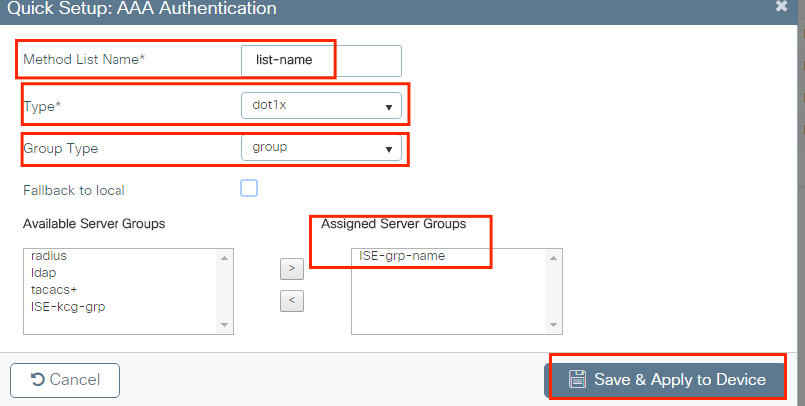
Enter the information:
CLI:
# config t # aaa new-model # radius server <radius-server-name> # address ipv4 <radius-server-ip> auth-port 1812 acct-port 1813 # timeout 300 # retransmit 3 # key <shared-key> # go out # aaa grouping server radius <radius-grp-proper noun> # server name <radius-server-name> # exit
# aaa server radius dynamic-author
# client <radius-server-ip> server-cardinal <shared-key>
# aaa authentication dot1x <dot1x-list-proper noun> group <radius-grp-name>
WLAN Contour Configuration
GUI:
Stride 1. Create the WLAN. Navigate toConfiguration > Wireless > WLANs > + Addand configure the network as needed.
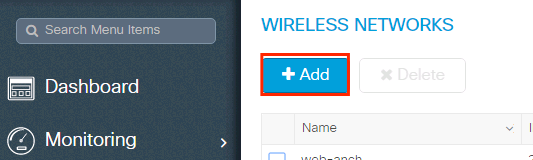
Footstep 2. Enter the WLAN data
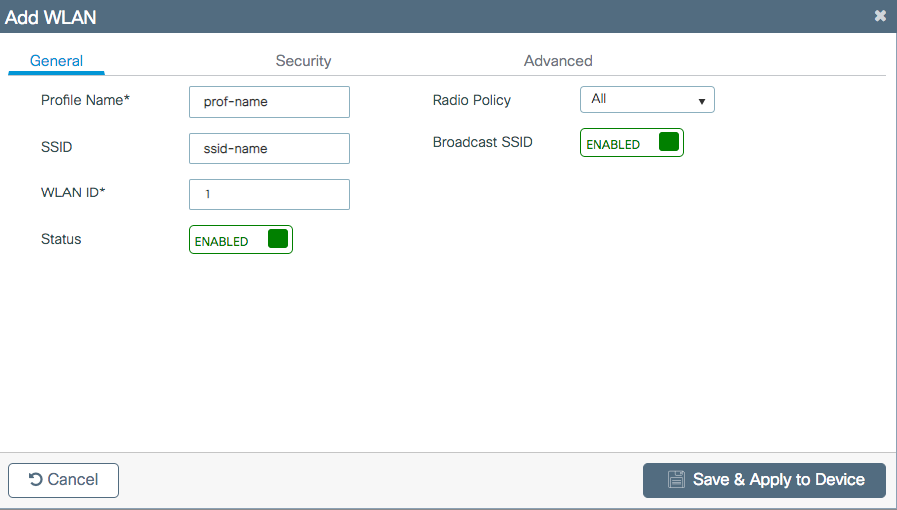
Step 3. Navigate toSecuritytab and select the needed security method. In this case WPA2 + 802.1x.
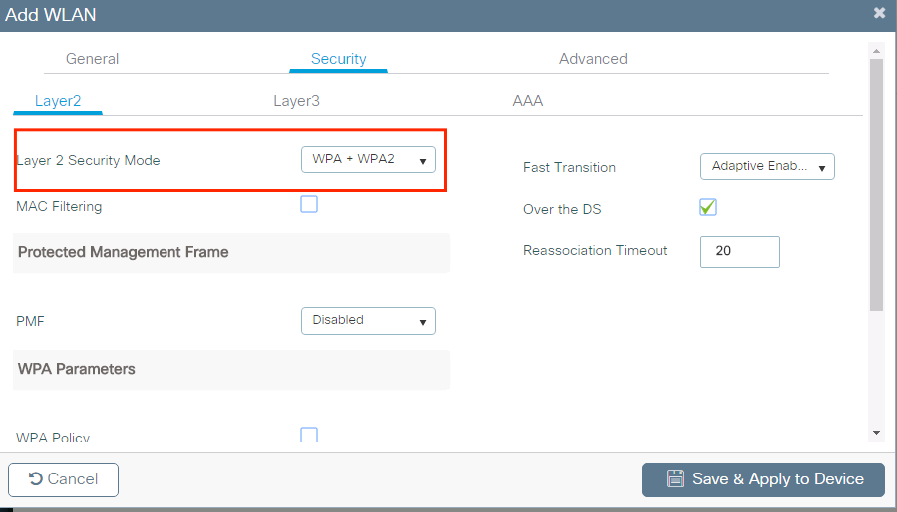
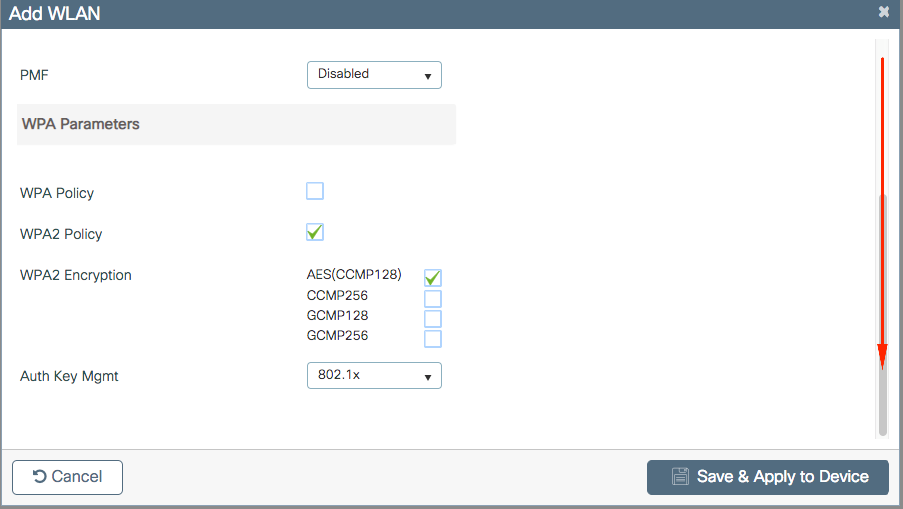
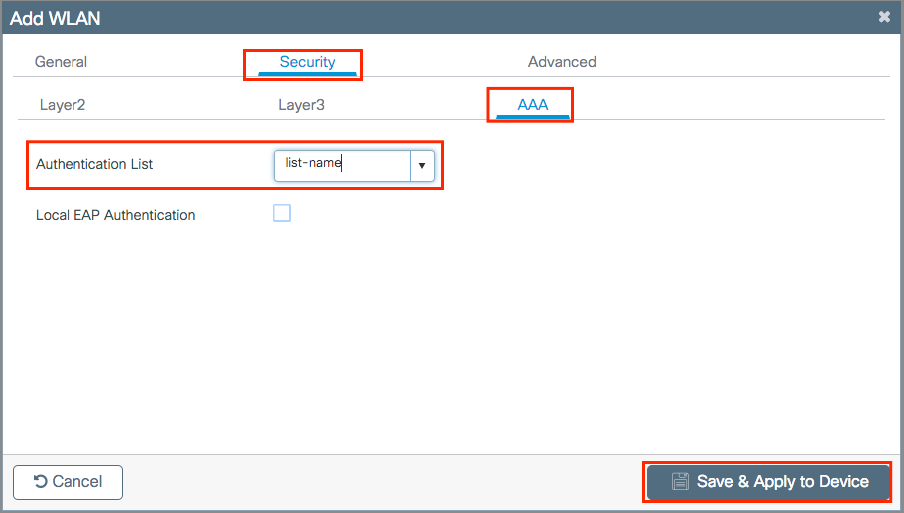
Step four. FromSecurity > AAAtab, select the authentication method created on pace 3 fromAAA Configuration on 9800 WLCsection.
CLI:
# config t # wlan <profile-name> <wlan-id> <ssid-name> # security dot1x authentication-listing <dot1x-listing-name> # no shutdown
Policy Profile Configuration
Within a Policy Profile yous can decide to which VLAN assign the clients, among other settings (like Access Controls List [ACLs], Quality of Service [QoS], Mobility Anchor, Timers and and then on).
You lot can either use your default policy profile or you can create a new.
GUI:
Navigate toConfiguration > Tags & Profiles > Policy Profileand either configure yourdefault-policy-profileor create a new one.
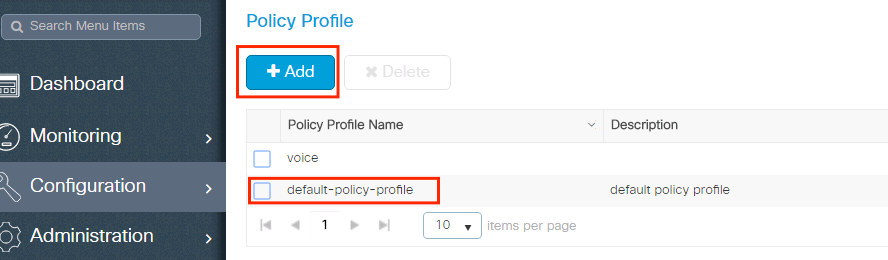
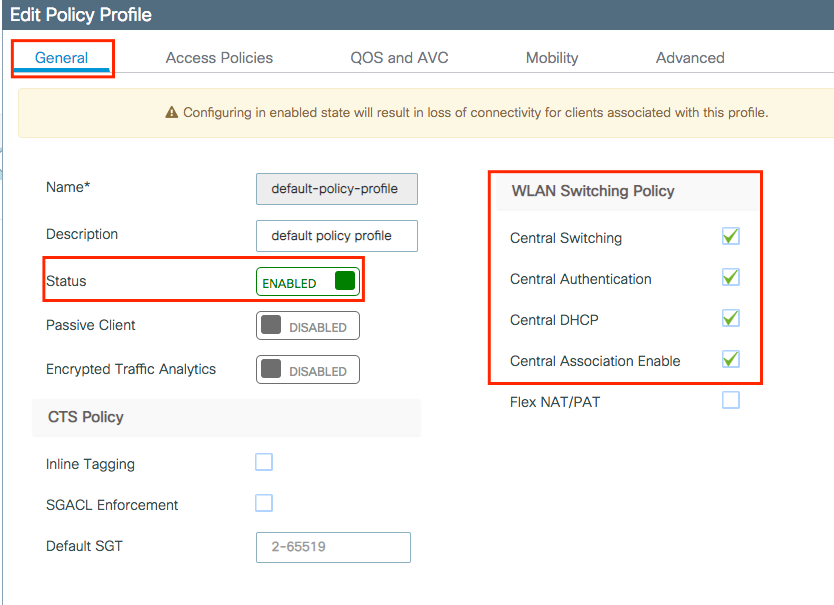
Ensure the profile is enabled.
As well, if your Access Point (AP) is in local mode, ensure the policy profile haveCentral SwitchingandCentral Authenticationenabled.
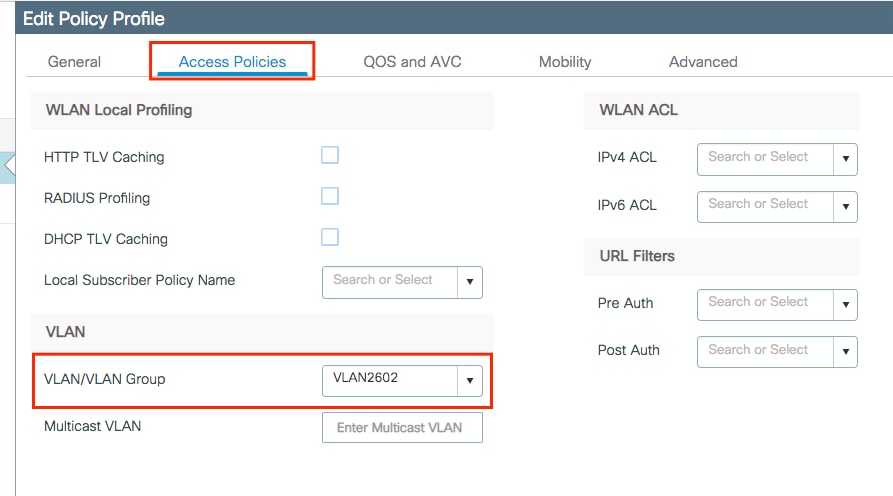
Select the VLAN where the clients need to be assigned in the Access Policies tab.
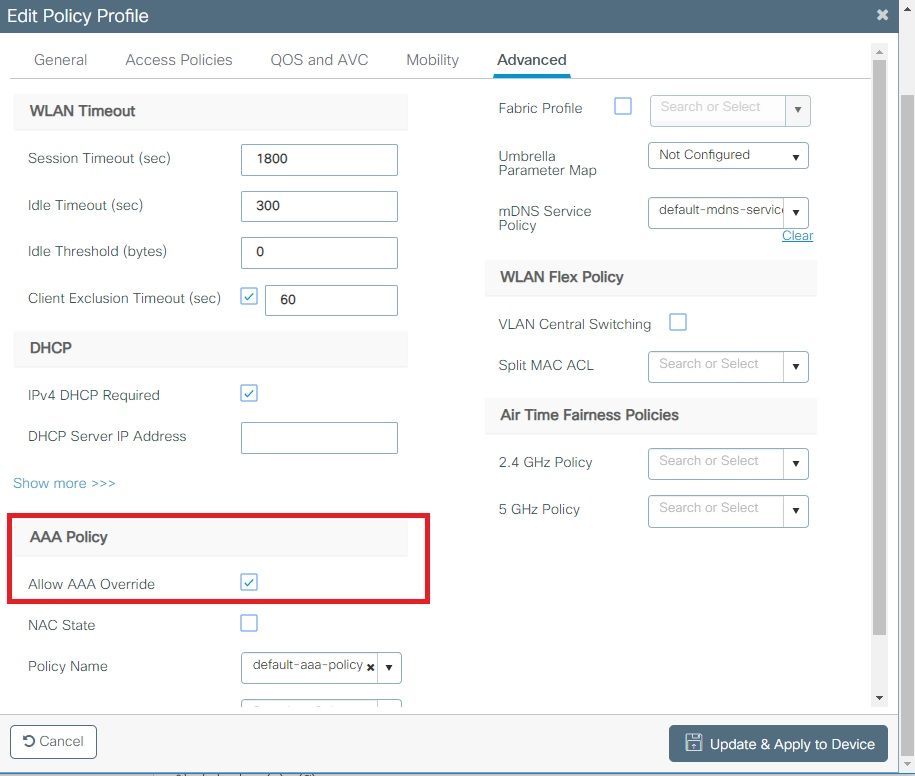
If you plan to have ISE return attributes in the Access-Accept like VLAN Assignment, please enable AAA override in the Avant-garde tab:
CLI:
# config # wireless contour policy <policy-profile-name>
# aaa-override # central switching # description "<clarification>" # vlan <vlanID-or-VLAN_name> # no shutdown
Policy Tag Configuration
Policy Tag is used to link the SSID with the Policy Profile. Yous can either create a new Policy Tag or use the default-policy tag.
Annotation:The default-policy-tag automatically maps any SSID with a WLAN ID between 1 to 16 to the default-policy-contour. It cannot be modified nor deleted.If you have a WLAN with ID 17 or higher, the default-policy-tag cannot be used.
GUI:
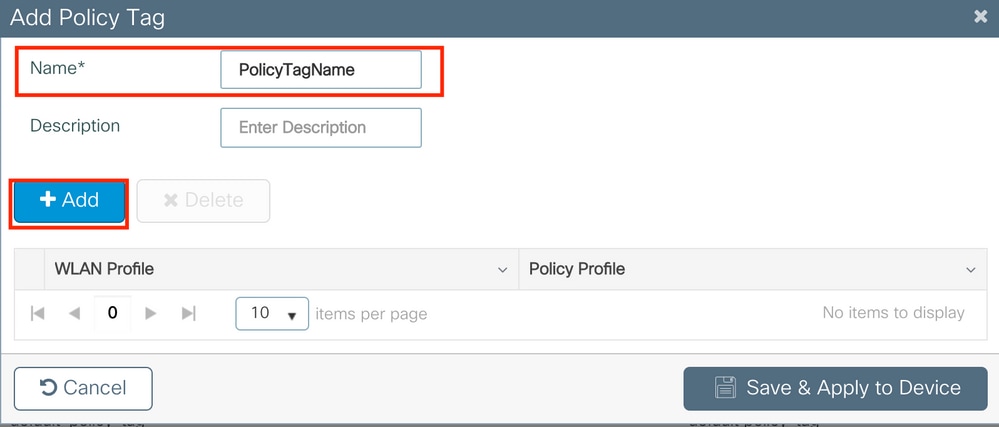
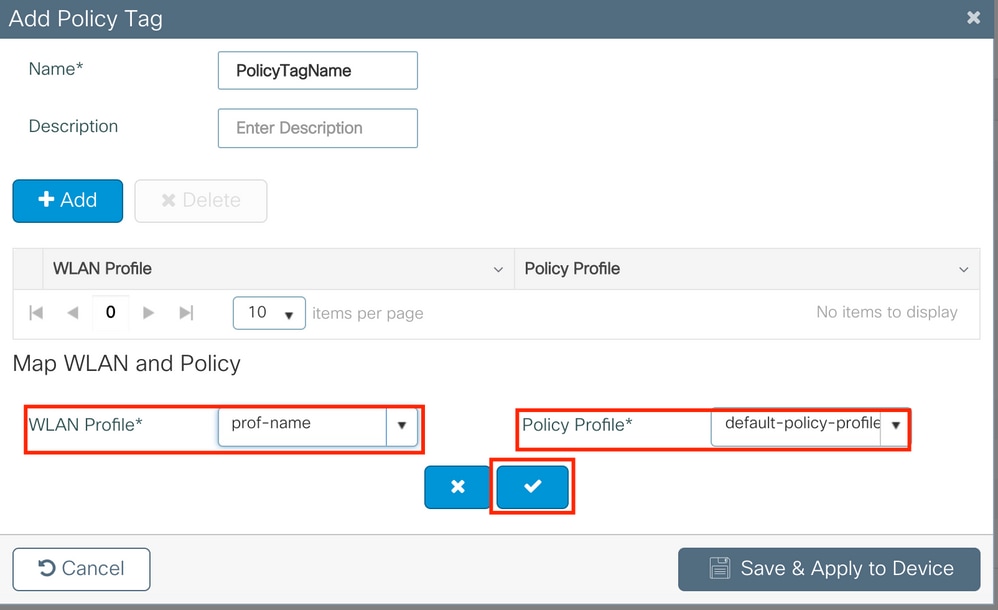
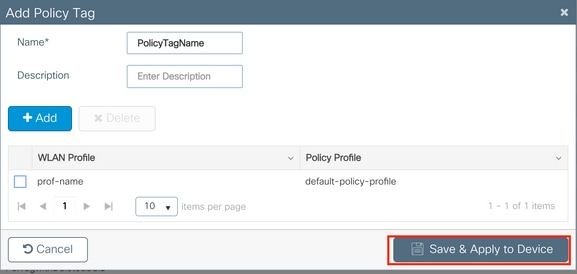
Navigate toConfigugation > Tags & Profiles > Tags > Policyand add a new one if needed.
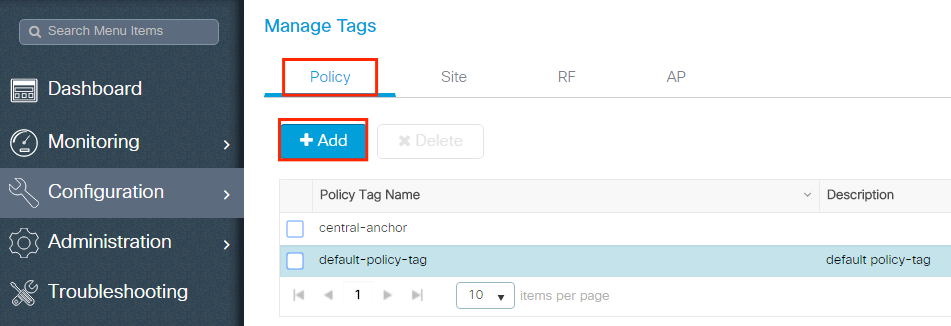
Link your WLAN Profile to the desired Policy Contour.
CLI:
# config t # wireless tag policy <policy-tag-name> # wlan <profile-name> policy <policy-contour-proper name>
Policy Tag Assignation
Assign the Policy Tag to the needed APs.
GUI:
To assign the tag to one AP, navigate toConfiguration > Wireless > Access Points > AP Name > Full general Tags, assign the relevant policy tag and then clickUpdate & Apply to Device.
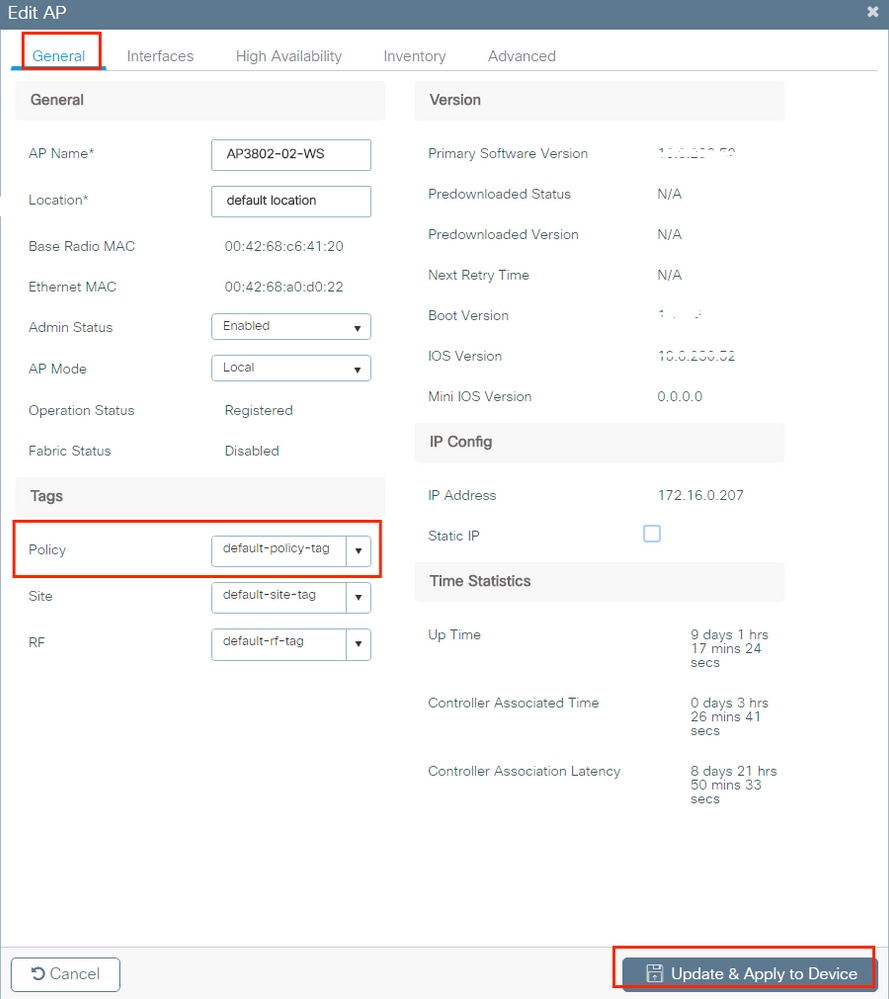
Annotation: Be aware that when the policy tag on an AP is changed, it drops its association to the 9800 WLC and volition bring together back.
To assign the same Policy Tag to several APs navigate toConfiguration > Wireless Setup > Advanced > Beginning At present > Use.
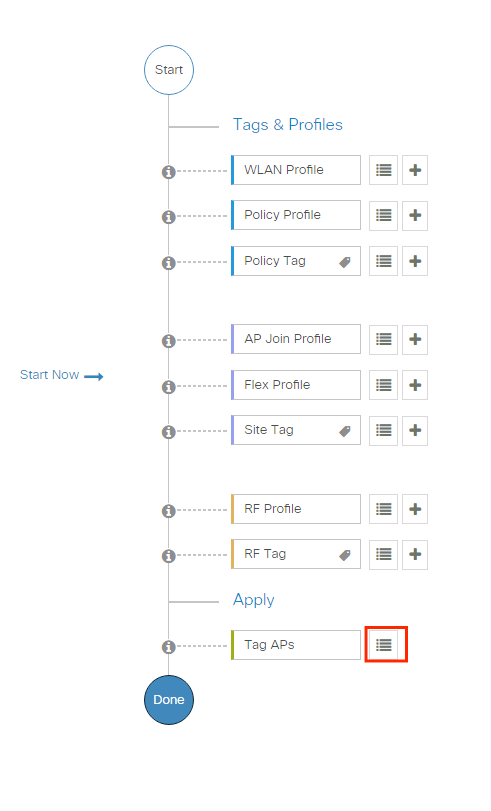
Select the APs to which you want to assign the tag and click+ Tag APs
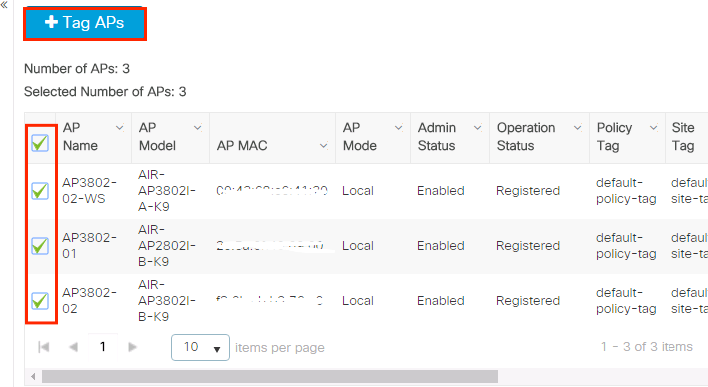
Select the applicable Tags for Policy, Site and RF and clickSave & Use to Device
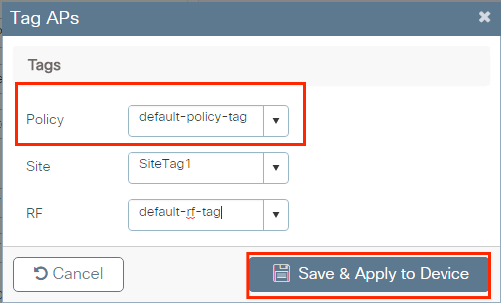
CLI:
# config t # ap <ethernet-mac-addr> # policy-tag <policy-tag-proper noun> # end
ISE Configuration
DeclareWLC onISE
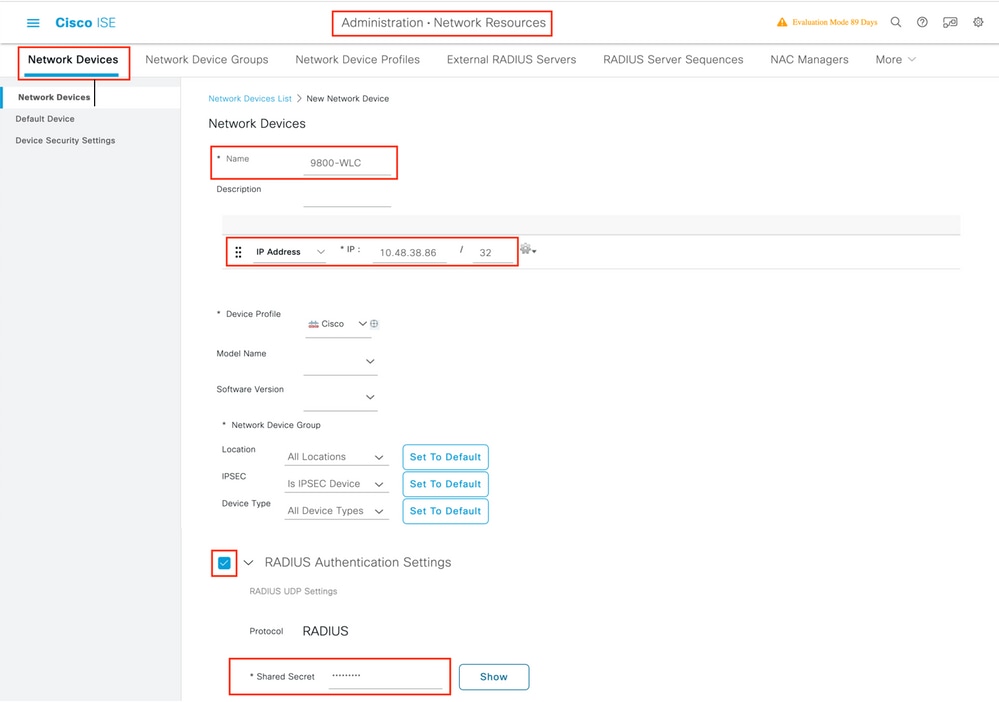
Pace 1. OpenISEconsoleandnavigate toAdministration > Network Resources > Network Devices > Add as shown in the paradigm.
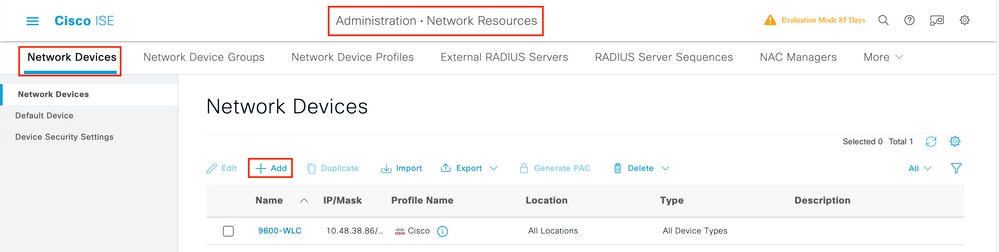
Stepii. Enter the values.
Optionally, it can be a specified Model name, software version, descriptionandassign Network Device groups based on device types, location or WLCs.
a.b.c.d correspond to the WLC's interface that sends thehallmarkrequested. By default it is the management interface equally shown in the image.
For more information aboutNetwork Device Groupsreview this link:
ISE - Network Device Groups
Create New User onISE
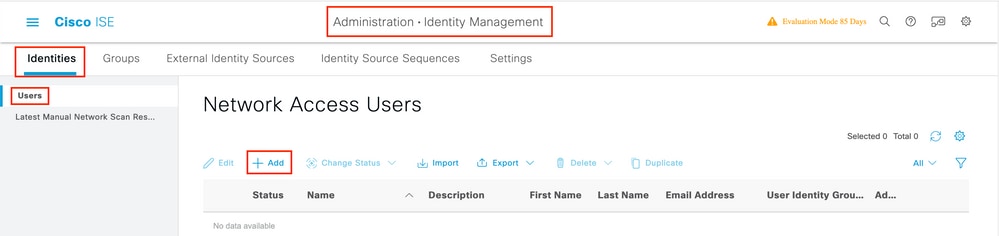
Step 1. Navigate toAdministration > Identity Management > Identities > Users > Addevery bit shown in the image.
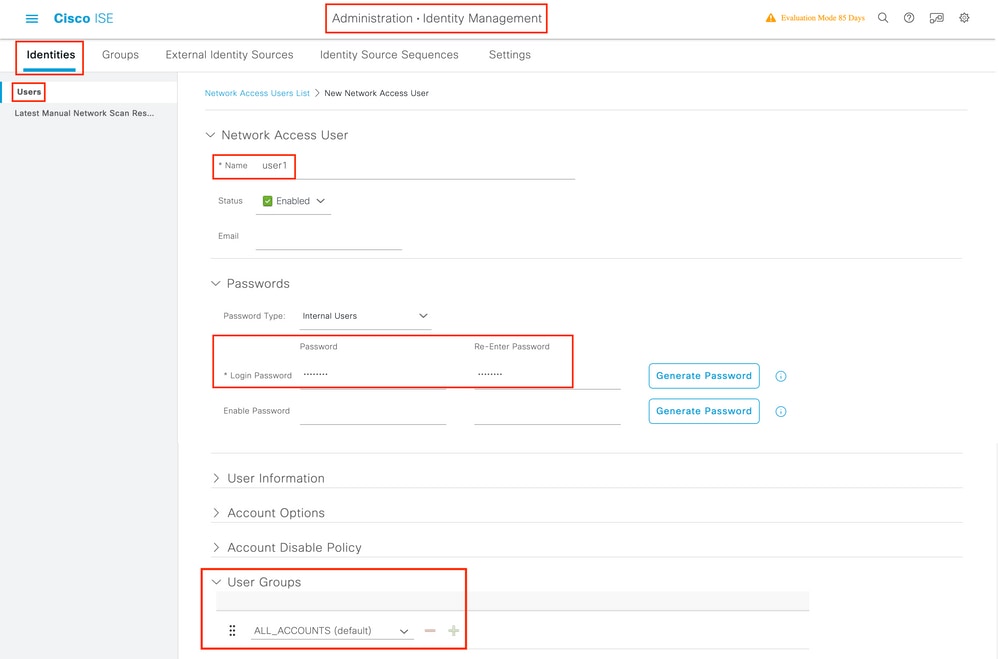
Stride2. Enter the information. In this example, this user belongs to a group called ALL_ACCOUNTS but information technology can be adjusted as needed as shown in the image.
CreateAuthentication Dominion
Hallmarkrules are used to verify if the credentials of the users are correct (verify if the user really is who it says information technology is)andlimit theauthenticationmethods that are allowed to exist used by it.
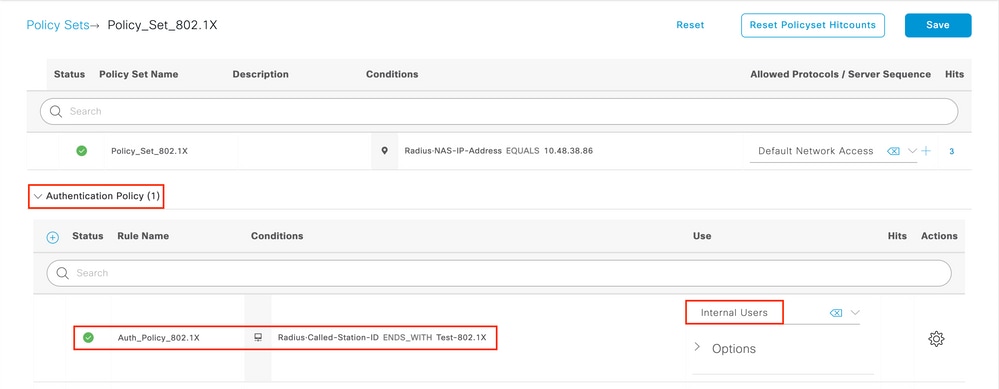
Step 1. Navigate toPolicy >Authentication as shown in the image.
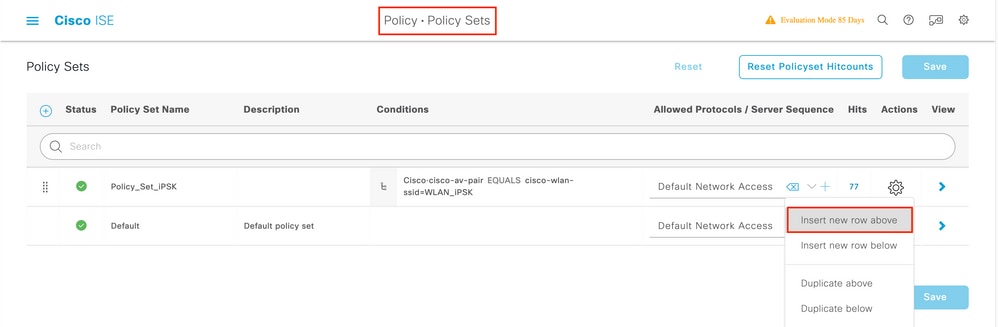
Step2. Insert a newauthenticationdominion as shown in the image.

Step 3. Enter the values. Thisauthenticationrule allows all the protocols listed under theDefault Network Access listing, this applies to theauthenticationrequest for Wireless802 .1xclientsand withCalled-Station-IDandendswith ise-ssidas shown in the image.
Also, choose the Identity Source for the clients that matches thisauthenticationdominion. This example usesInternal Users identity source listing as shown in the prototype.
Once finished, clickDone and Salveas shown in the prototype.
For more data about Allow Protocols Policies consult this link:
Allowed Protocols Service
For more information about Identity sources consult this link:
Create a User Identity Group
Create Authorization Contour
The authorization profile determines if the client has access or not to the network, push Admission Command Lists (ACLs), VLAN override or any other parameter. The authorization profile shown in this example sends an admission accept for the clientandassigns the client to VLAN 2404.
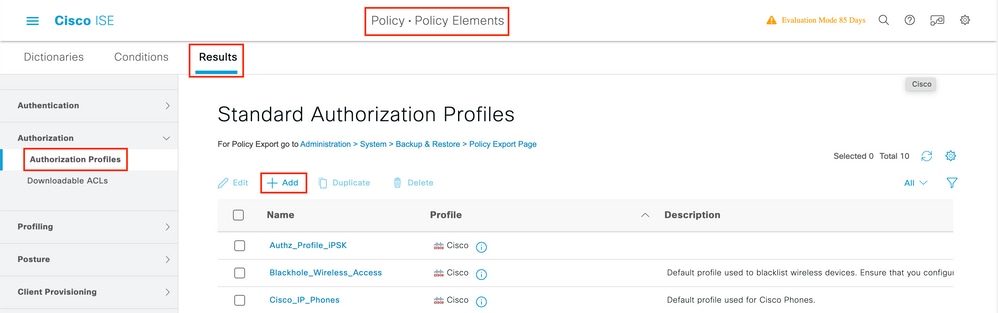
Step one. Navigate toPolicy > Policy Elements > Resultsas shown in the image.
Step2. Add a new Authorization Profile. Navigate toAuthorisation > Dominance Profiles > Addas shown in the paradigm.
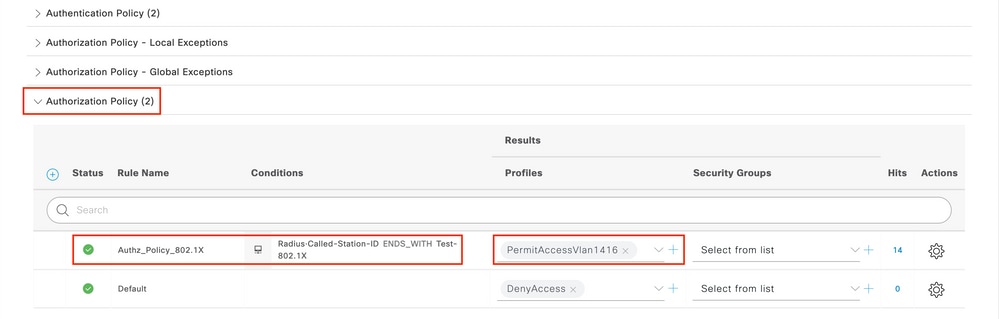
Pace 3. Enter the values as shown in the image. Here nosotros can render AAA override attributes like VLAN as example. WLC 9800 accepts tunnel attributes 64,65,81 using VLAN id or Name, and accepts also the usage of the AirSpace-Interface-Name Attribute.
Create Authorization Rule
The authorisation rule is the one in charge to decide which permissions (which authorization profile) issue is practical to the client.
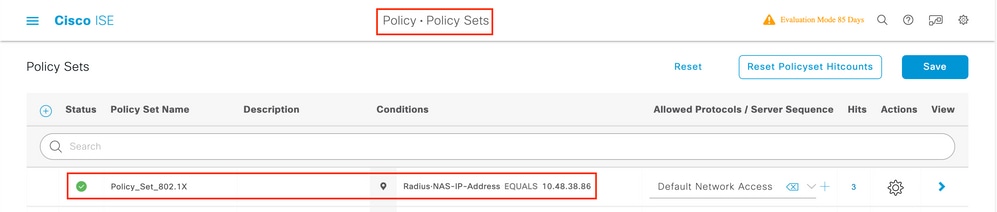
Step 1. Navigate toPolicy > Potencyas shown in the epitome.
Steptwo. Insert a new dominion as shown in the image.
Footstep three. Enter the values. Offset, select a name for the dominionandthe Identity group where the user is stored (ALL_ACCOUNTS) as shown in the image.
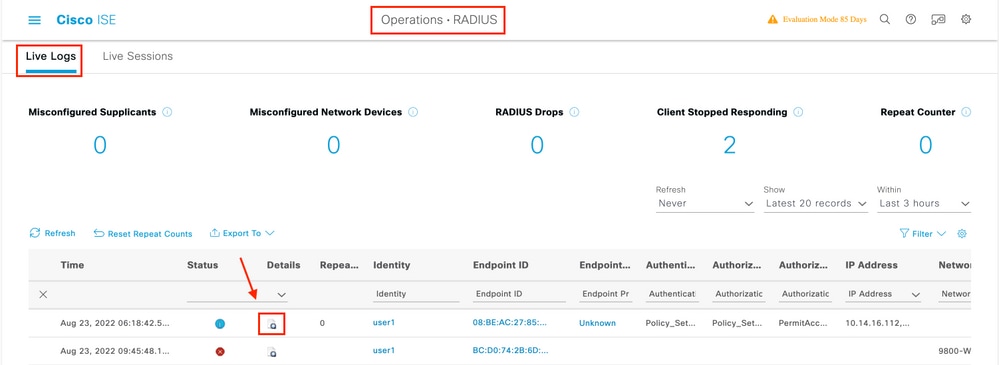
Afterwards that, select other atmospheric condition that practise the authorization procedure to fall into this dominion. In this example, the authorization process hits this rule if information technology uses802 .1xWirelessandits chosen station ID endswith ise-ssidas shown in the prototype.

Finally, select the Authorization contour that is assigned to the clients that hitting that dominion, clickWashed andsave information technology as shown in the image.

You tin can use these commands to verify current configuration
# show run wlan # show run aaa # show aaa servers # bear witness ap config general # testify ap name <ap-name> config full general
# prove ap tag summary
# show ap <ap-name> tag detail
# evidence wlan { summary | id | name | all }
# show wireless tag policy detailed <policy-tag name>
# testify wireless profile policy detailed <policy-profile proper name>
WLC 9800 provides Always-ON tracing capabilities. This ensures all customer connectivity related errors, wanring and detect level letters are constantly logged and y'all can view logs for an incident or failure status after it has occurred.
Note: Depending on volume of logs beingness generated, y'all can become back few hours to several days.
In guild to view the traces that 9800 WLC collected by default, yous can connect via SSH/Telnet to the 9800 WLC and follow these steps (Ensure y'all are logging the session to a text file).
Step 1. Check controller's current time so you tin track the logs in the time back to when the event happened.
# bear witness clock
Step 2. Collect syslogs from the controller's buffer or the external syslog equally dictated past the system configuration. This provides a quick view into the system health and errors, if any.
# evidence logging
Pace iii. Verify if any debug conditions are enabled.
# testify debugging IOSXE Conditional Debug Configs: Conditional Debug Global Land: Stop IOSXE Bundle Tracing Configs: Parcel Infra debugs: Ip Address Port ------------------------------------------------------|----------
Note: If you see any status listed, it means the traces are existence logged upward to debug level for all the processes that encounter the enabled weather condition (mac address, ip accost etc). This would increase the volume of logs. Therefore, it is recommended to clear all weather when non actively debugging
Step iv. Assuming mac address under exam was non listed equally a condition in Footstep three, collect the ever-on notice level traces for the specific mac address.
# testify logging profile wireless filter { mac | ip } { <aaaa.bbbb.cccc> | <a.b.c.d> } to-file always-on-<FILENAME.txt> You can either display the content on the session or y'all tin can copy the file to an external TFTP server.
# more than bootflash:always-on-<FILENAME.txt>
or
# copy bootflash:e'er-on-<FILENAME.txt> tftp://a.b.c.d/path/always-on-<FILENAME.txt>
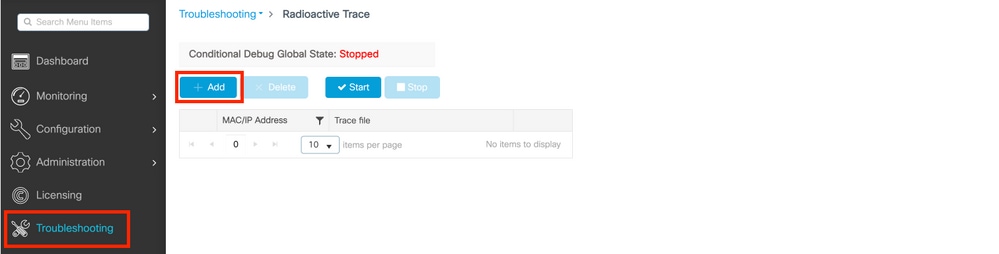
Provisional Debugging and Radio Agile Tracing
If the always-on traces practice not give you enough information to make up one's mind the trigger for the problem under investigation, you can enable conditional debugging and capture Radio Active (RA) trace, which will provide debug level traces for all processes that interact with the specified condition (client mac address in this case). In order to enable conditional debugging, follow these steps.
Step 5. Ensure there are no debug weather are enabled.
# clear platform condition all
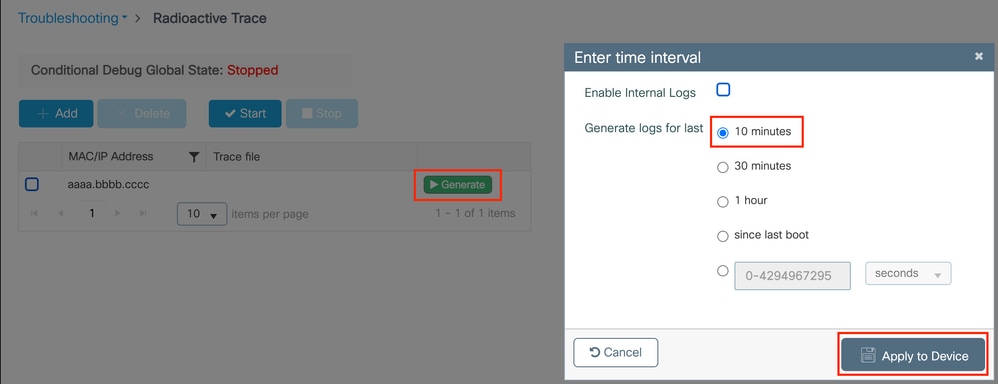
Step 6. Enable the debug status for the wireless client mac address that y'all want to monitor.
This commands start to monitor the provided mac address for xxx minutes (1800 seconds). You can optionally increase this time to up to 2085978494 seconds.
# debug wireless mac <aaaa.bbbb.cccc> {monitor-time <seconds>} Note:In lodge to monitor more than than ane client at a time, run debug wireless mac <aaaa.bbbb.cccc> command per mac address.
Notation:You lot do not see the output of the client activity on concluding session, as everything is buffered internally to be viewed subsequently.
Step 7. Reproduce the issue or behavior that you want to monitor.
Step eight. Cease the debugs if the issue is reproduced before the default or configured monitor time is upward.
# no debug wireless mac <aaaa.bbbb.cccc>
Once the monitor-time has elapsed or the debug wireless has been stopped, the 9800 WLC generates a local file with the proper noun:
ra_trace_MAC_aaaabbbbcccc_HHMMSS.XXX_timezone_DayWeek_Month_Day_year.log
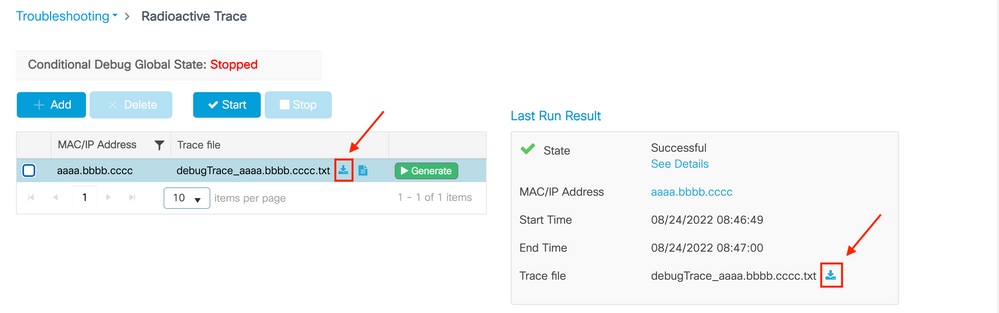
Step 9.Collect the file of the mac address activity. You tin can either re-create the ra trace .log to an external server or brandish the output direct on the screen.
Bank check the name of the RA traces file
# dir bootflash: | inc ra_trace
Re-create the file to an external server:
# re-create bootflash:ra_trace_MAC_aaaabbbbcccc_HHMMSS.XXX_timezone_DayWeek_Month_Day_year.log tftp://a.b.c.d/ra-FILENAME.txt Display the content:
# more bootflash:ra_trace_MAC_aaaabbbbcccc_HHMMSS.XXX_timezone_DayWeek_Month_Day_year.log Step ten. If the root crusade is nevertheless not obvious, collect the internal logs which are a more verbose view of debug level logs. You lot practice not need to debug the client again as we are only taking a futher detailed expect at debug logs that take been already colllected and internally stored.
# show logging profile wireless internal filter { mac | ip } { <aaaa.bbbb.cccc> | <a.b.c.d> } to-file ra-internal-<FILENAME>.txt Annotation: This command output returns traces for all logging levels for all processes and is quite voluminous. Please engage Cisco TAC to aid parse through these traces.
You tin either re-create the ra-internal-FILENAME.txt to an external server or display the output directly on the screen.
Re-create the file to an external server:
# re-create bootflash:ra-internal-<FILENAME>.txt tftp://a.b.c.d/ra-internal-<FILENAME>.txt
Display the content:
# more bootflash:ra-internal-<FILENAME>.txt
Pace eleven. Remove the debug conditions.
# articulate platform condition all
Note: Ensure that you lot always remove the debug conditions later on a troubleshooting session.
Source: https://www.cisco.com/c/en/us/support/docs/wireless/catalyst-9800-series-wireless-controllers/213919-configure-802-1x-authentication-on-catal.html
Posted by: clyburnnotle1973.blogspot.com

0 Response to "How To Enable 802.1 X On Windows 10"
Post a Comment